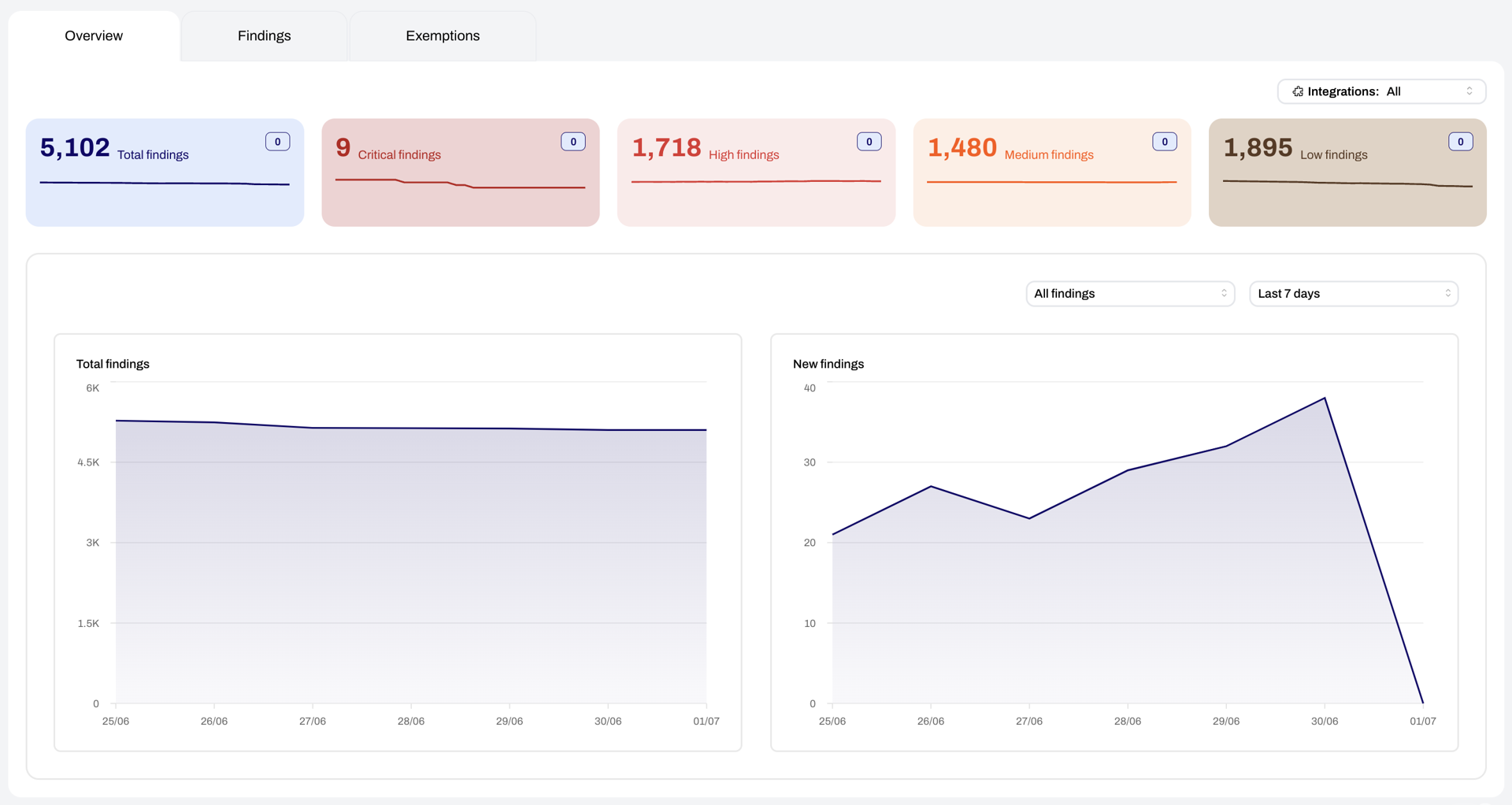
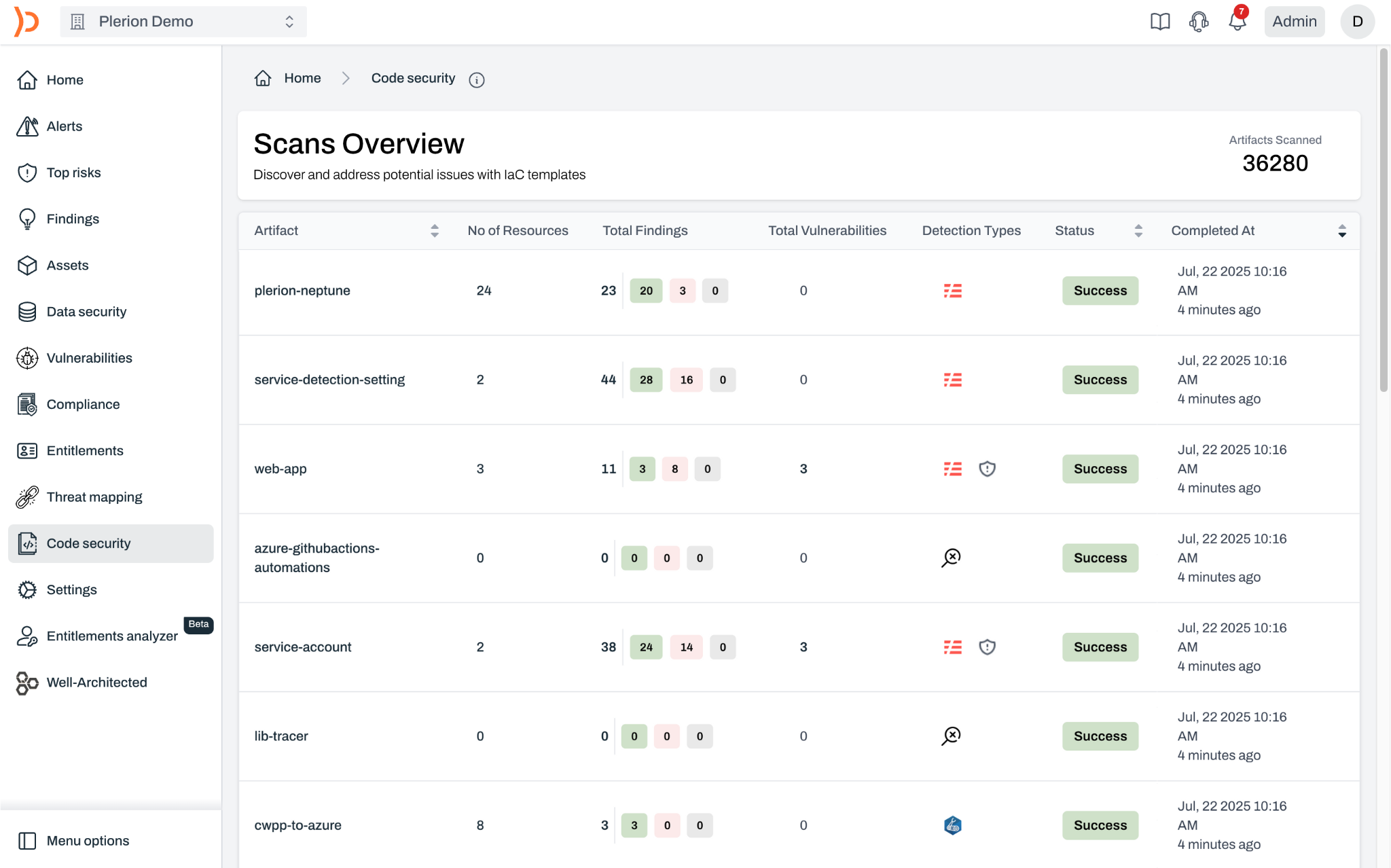
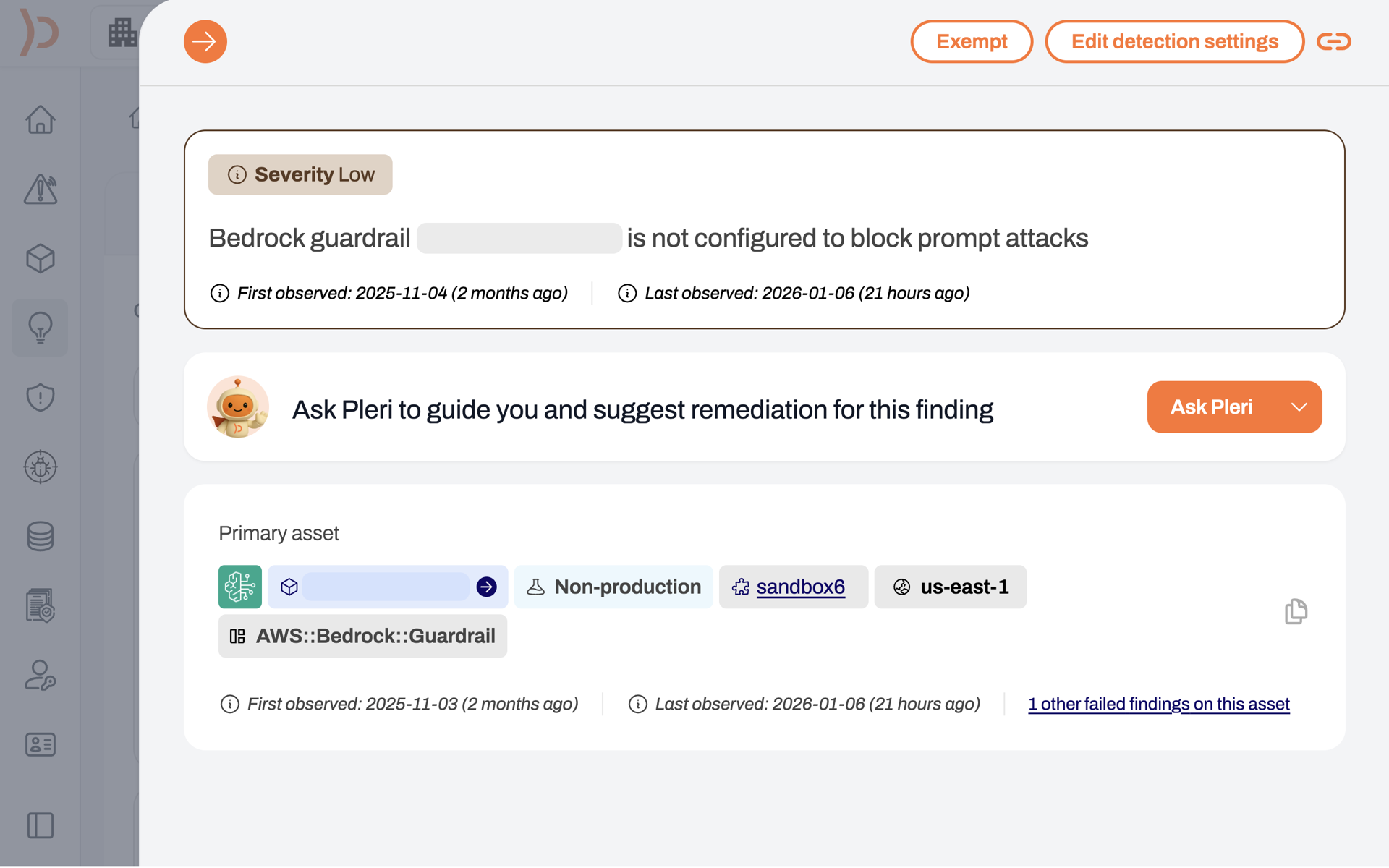
Want to know what software is installed on all of your cloud workloads? We generate a complete Software Bill of Materials (SBOM) for each workload. Each SBOM is generated in an open JSON format so it can be consumed by other tools.View software packages deployed across systems, assess third-party software dependencies, and track dependencies between open source components.